the-events-calendar/tribe-events-calendar-de_DE.po at master · nesciens/the-events-calendar · GitHub

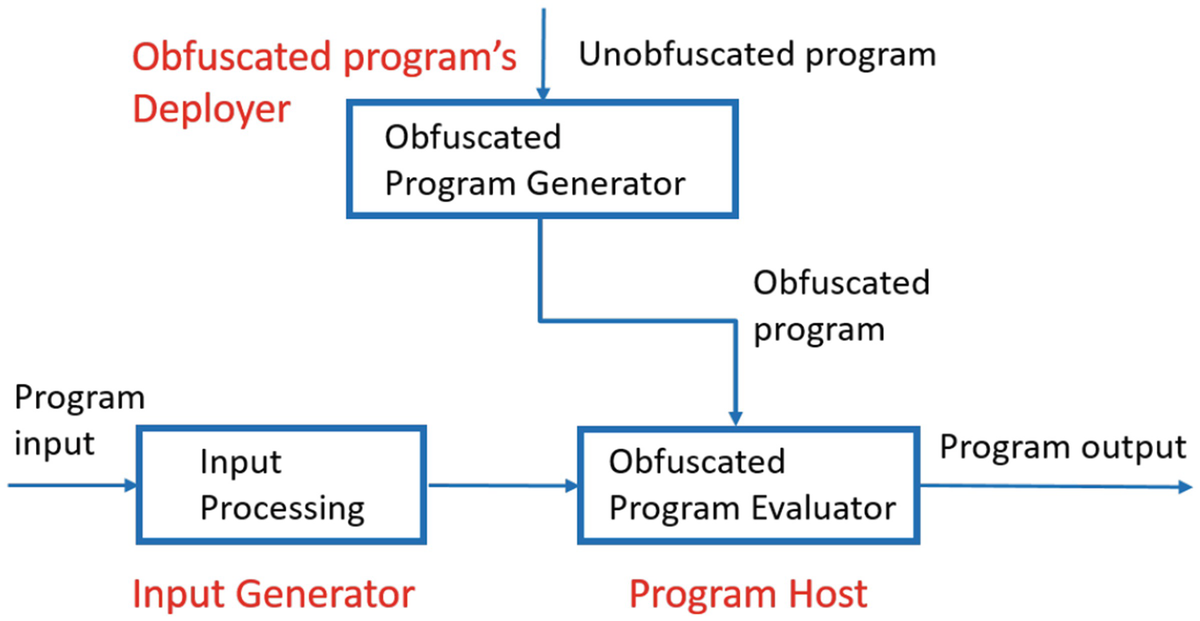
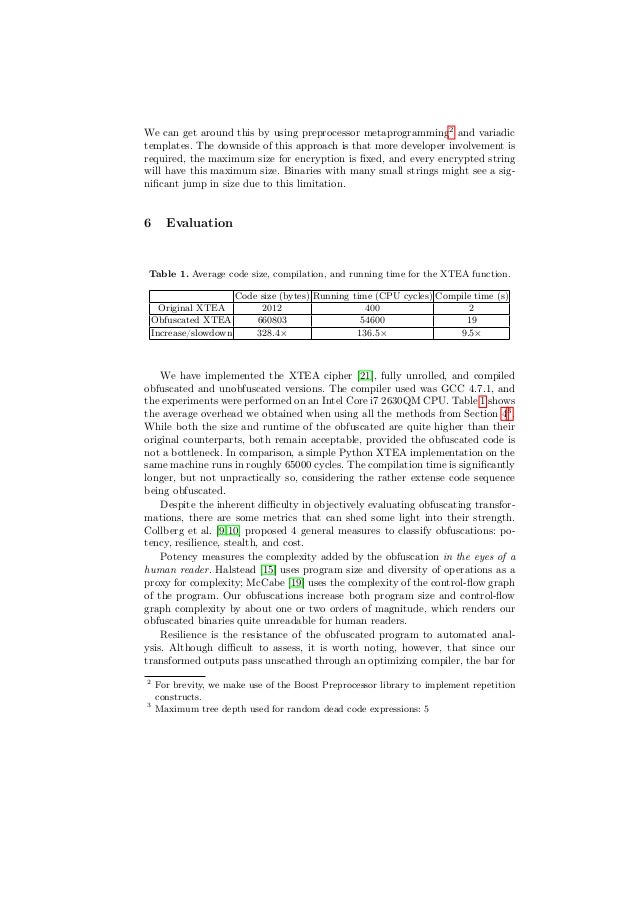
Theoretical Foundation for Code Obfuscation Security: A Kolmogorov Complexity Approach | SpringerLink

PDF) Security Against Hardware Trojan Attacks Through a Novel Chaos FSM and Delay Chains Array PUF Based Design Obfuscation Scheme
PDF) Assessing the Impacts of Species Composition on the Accuracy of Mapping Chlorophyll Content in Heterogeneous Ecosystems
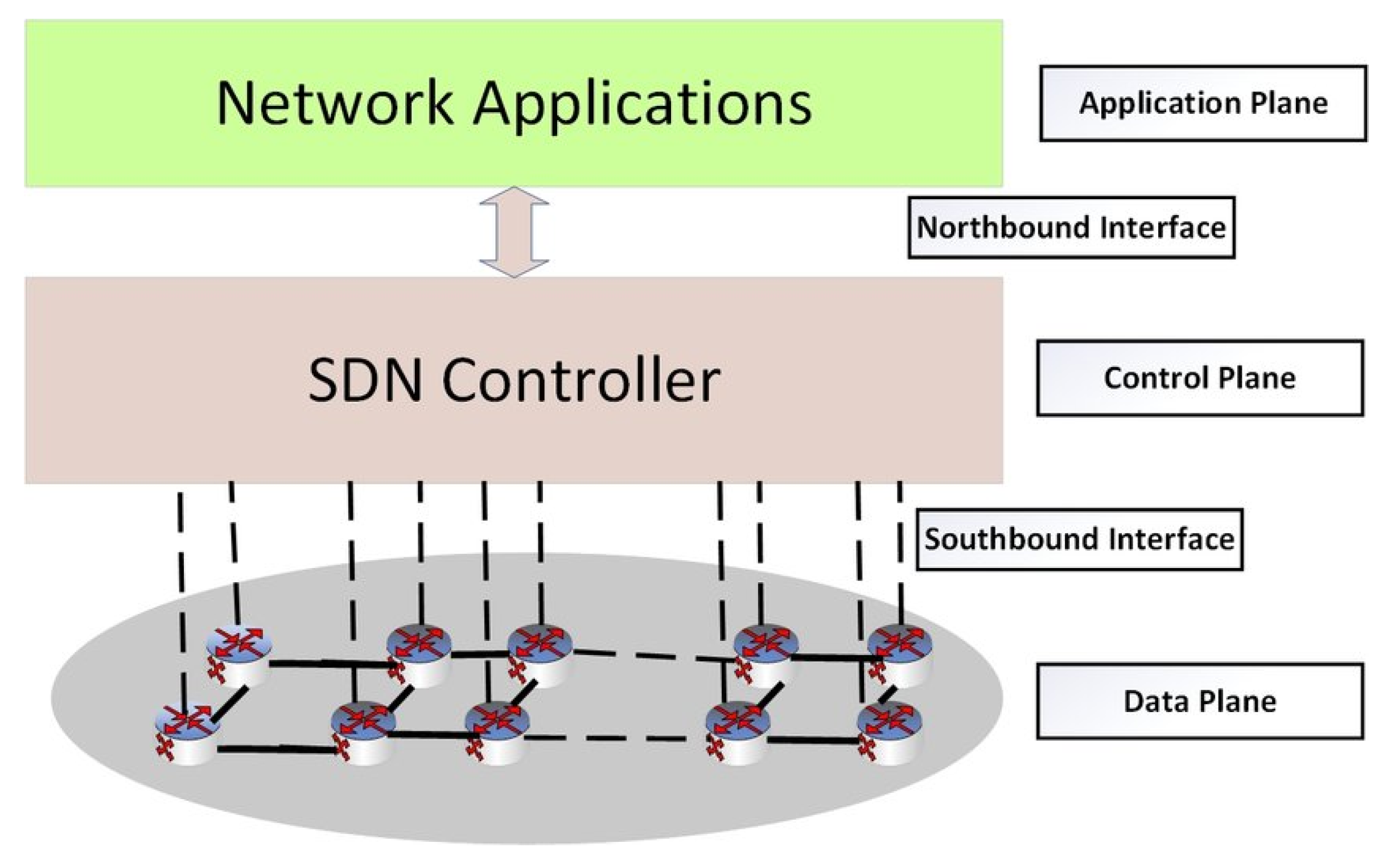
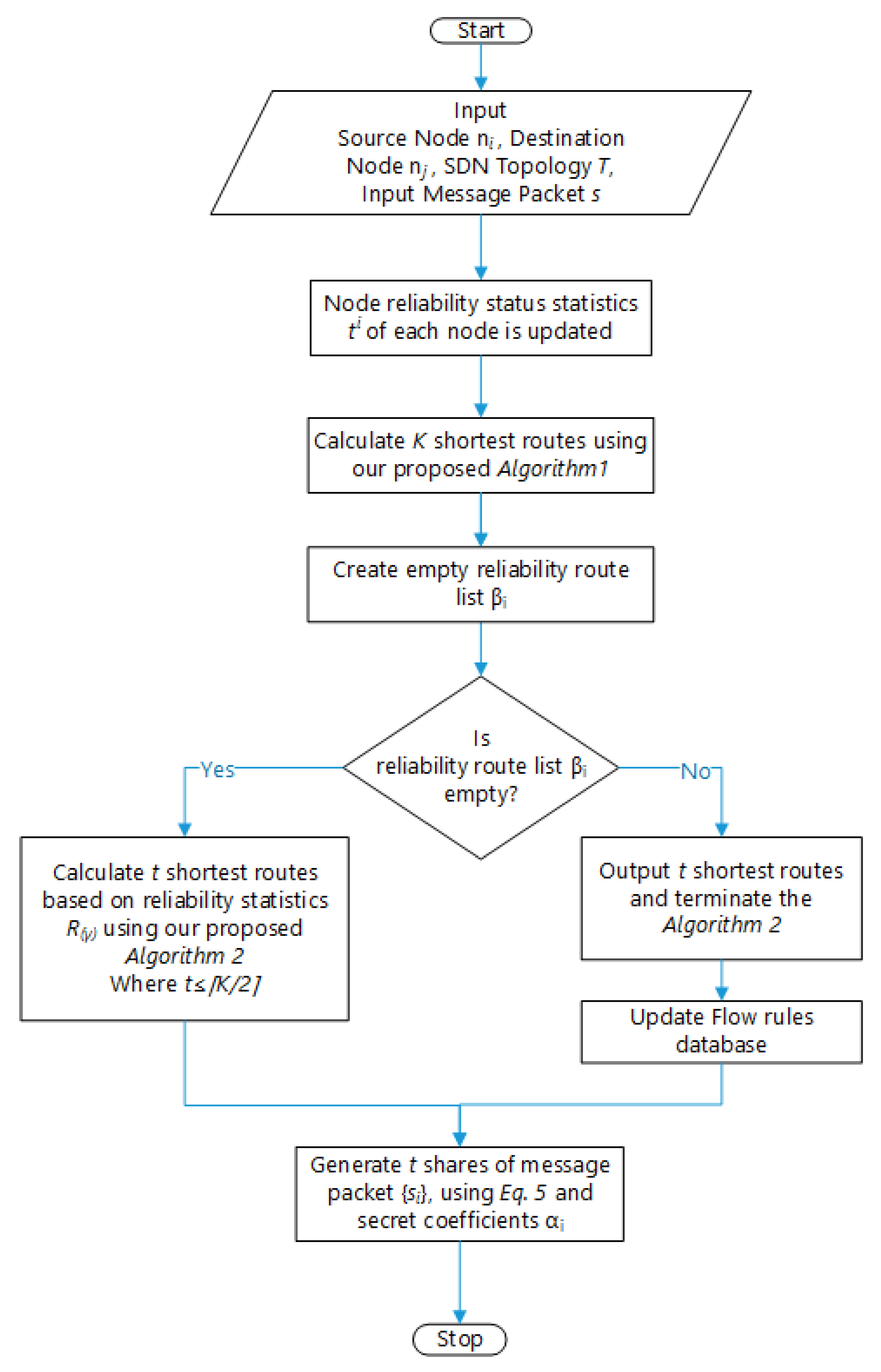
Sensors | Free Full-Text | Secure Route-Obfuscation Mechanism with Information-Theoretic Security for Internet of Things | HTML

Lattice‐based obfuscation for re‐encryption functions - Cheng - 2015 - Security and Communication Networks - Wiley Online Library

Starting with Minecraft snapshot 19w36a, obfuscation mappings are published with the game. What does this mean for us? : r/feedthebeast

Lattice‐based obfuscation for re‐encryption functions - Cheng - 2015 - Security and Communication Networks - Wiley Online Library
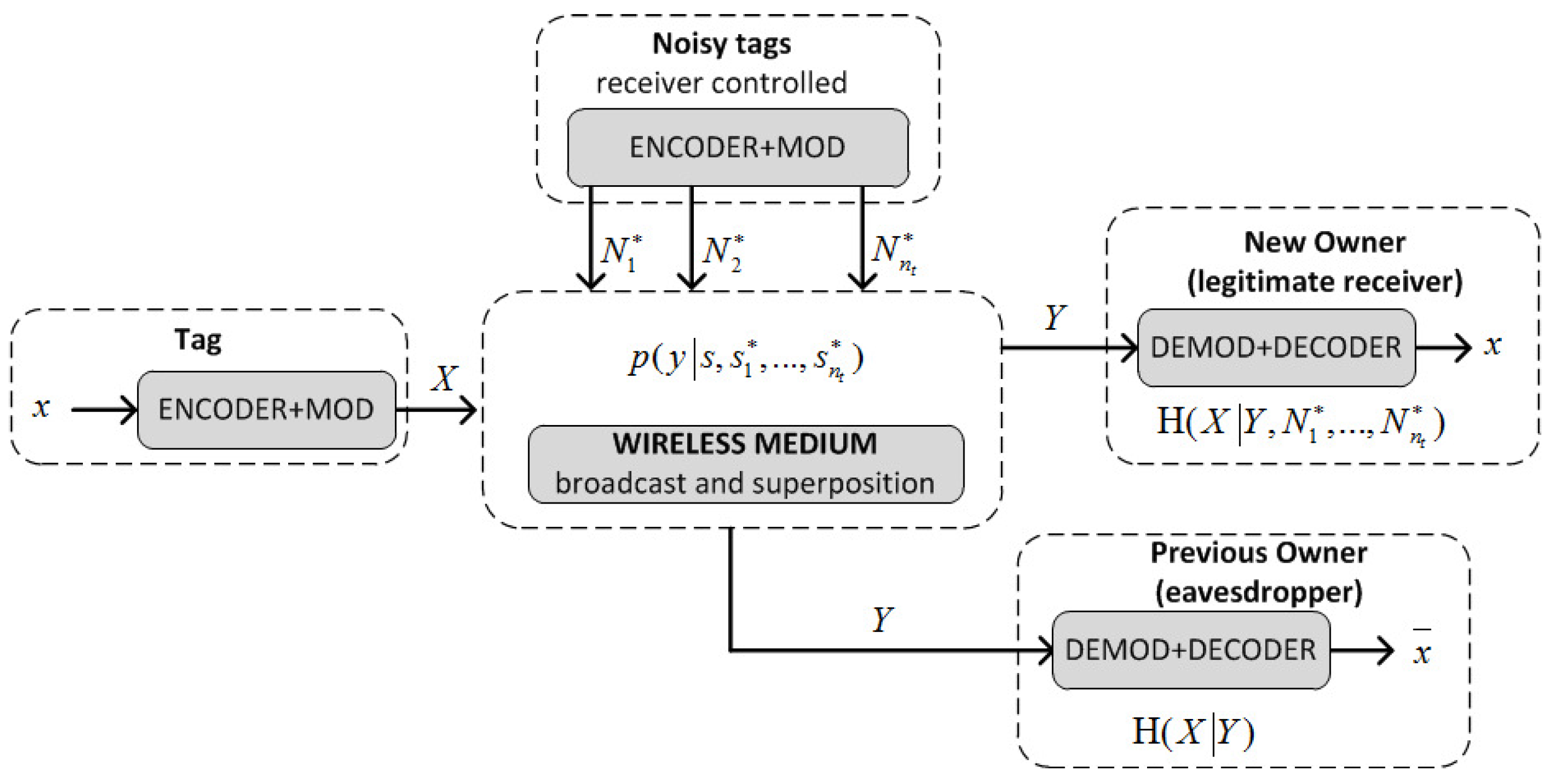
Sensors | Free Full-Text | An RFID-Based Smart Structure for the Supply Chain: Resilient Scanning Proofs and Ownership Transfer with Positive Secrecy Capacity Channels | HTML